
SecurityCoach

Real-Time Coaching in Response to Risky Security Behavior
SecurityCoach is the first real-time security coaching product that leverages Human Detection and Response (HDR) to help protect your organization’s largest attack surface—your employees.
How Does SecurityCoach Work?
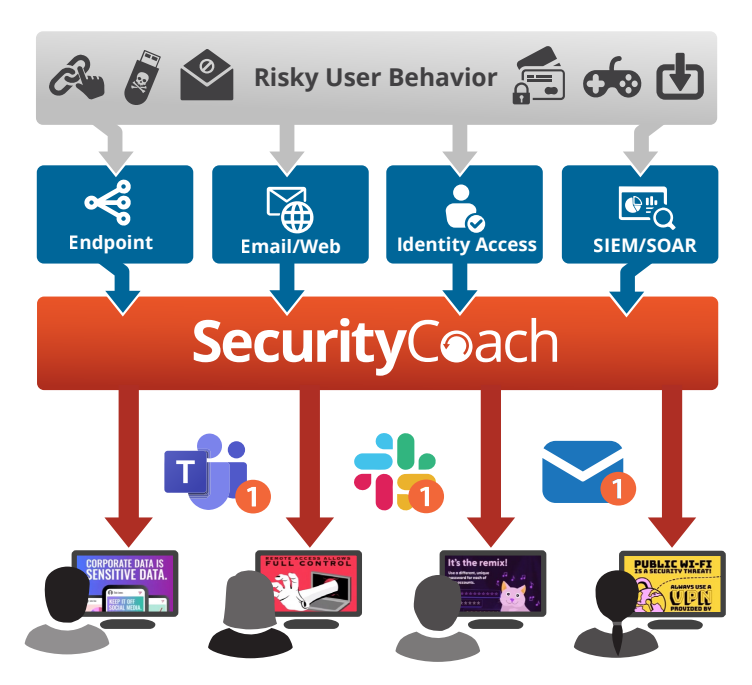
SecurityCoach uses standard APIs to quickly and easily integrate with your existing security products from vendors like Microsoft, CrowdStrike, Cisco and dozens of others. Your security stack generates alerts that are then analyzed by SecurityCoach to identify events related to any risky security behavior from your users.
For example, if a user opens an infected email attachment which might spread ransomware in your network, or tries to visit a website with restricted content on their work computer, your security products detect this and create an event alert. SecurityCoach identifies that event and then, via Microsoft Teams, Slack or email, sends a real-time SecurityTip to that user acknowledging that “Hey, this is a security risk and here’s why.” You can set up coaching campaigns to target risky users based on those events from your network, identity, web security and other vendors within your security stack. These campaigns enable you to coach your users at the moment the risky behavior occurs, providing real-time feedback and reinforcing the security awareness training campaigns you run today. Using your own security policies as a foundation and assisted by SecurityCoach automation settings, you can easily configure real-time coaching campaigns.
SecurityCoach reinforces the need to follow your organization’s security policies, improving user behavior and strengthening your overall security culture.
Features and Capabilities
Real-Time Coaching
Strengthen your organization’s security culture by delivering immediate feedback to your users at the moment risky behavior occurs.
API-Based Vendor Integrations
Quickly and easily integrate SecurityCoach with your existing security stack to share alert data on detected user events that present risk to your organization.
Built-In Detection Rules
Detection rules allow your IT and Security Operations teams to specify and customize exactly what types of risky behavior they want to track.
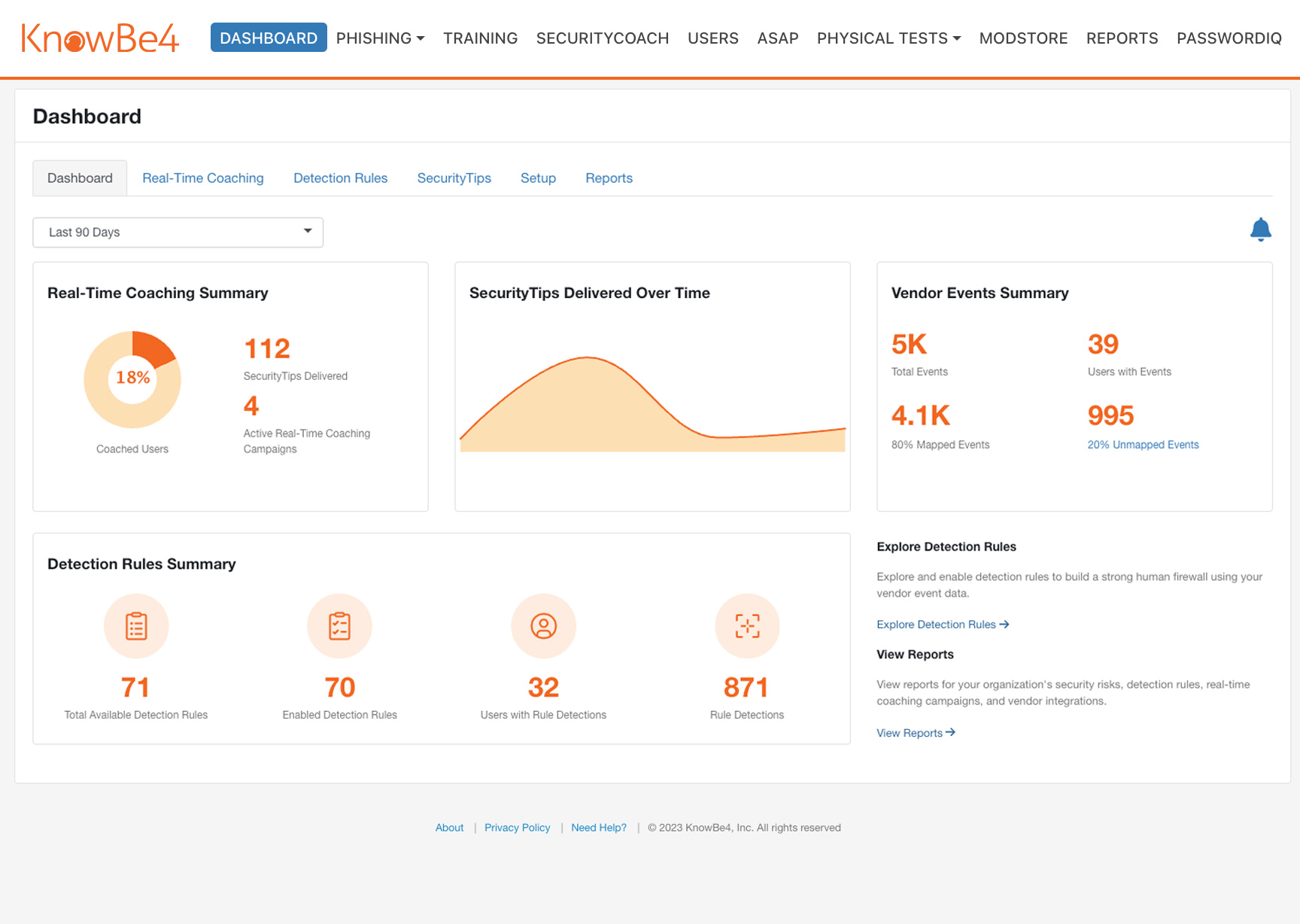
Dashboard and Detailed Reporting
Take a data-driven approach to quantifying and reducing human risk with a built-in dashboard that provides an overall summary of coaching campaigns, detection rules and detected security events.
Hear from Peers Who Are Driving Security Awareness Success
The ability to deliver live coaching via email, teams, or chat at the moment of action is fantastic.
Mid-market staffing and recruiting agency
Overall, SecurityCoach is a valuable resource for our company that improves knowledge about cybersecurity. It’s user-friendly, easy to navigate, and intuitive.
Healthcare and biotech company
It’s the best product I’ve seen to help IT and security operation teams.
Government Agency
Seamless Integrations: Fortifying Your Security Ecosystem

